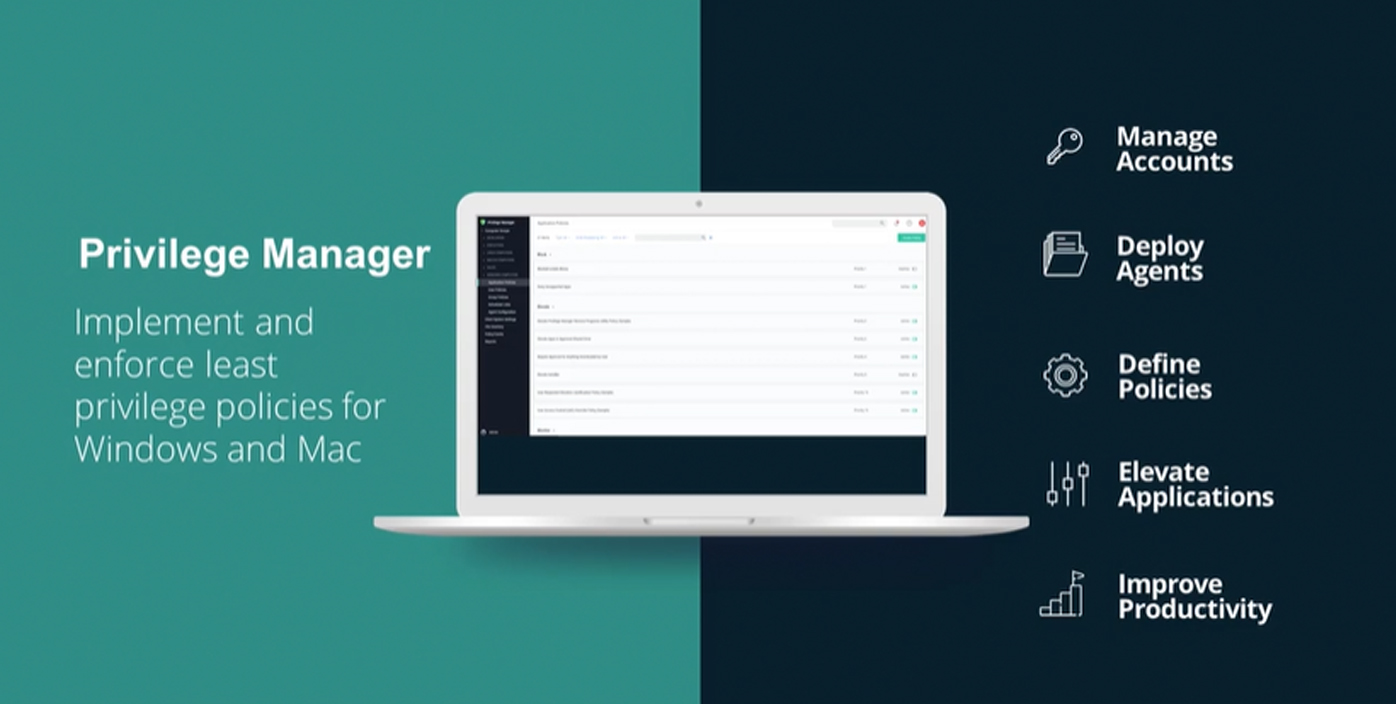
- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 25 September 2020 13:24

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 11 September 2020 14:06

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 25 September 2020 13:09

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 11 September 2020 14:00

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 25 September 2020 12:55

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 11 September 2020 13:43

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 25 September 2020 12:48

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 11 September 2020 13:15
- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 25 September 2020 12:36

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Thursday, 10 September 2020 16:46
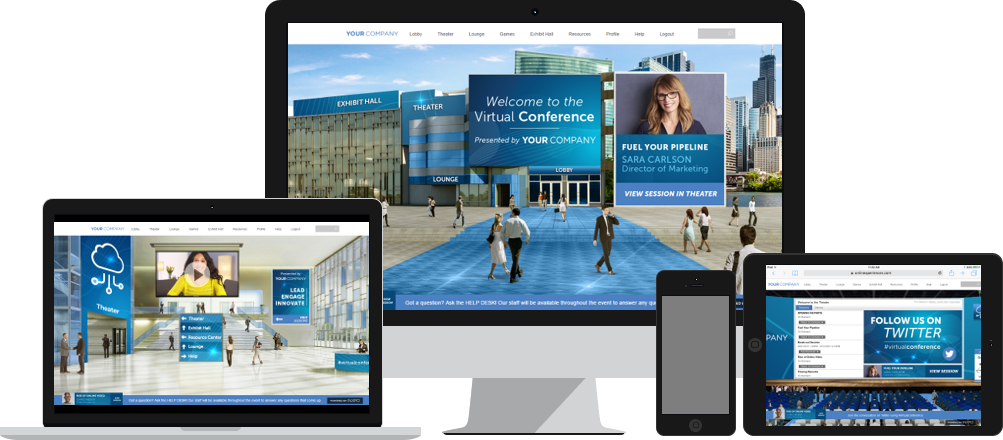
- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 25 September 2020 12:27

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Thursday, 03 September 2020 16:59

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 18 September 2020 13:04

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Thursday, 03 September 2020 15:28
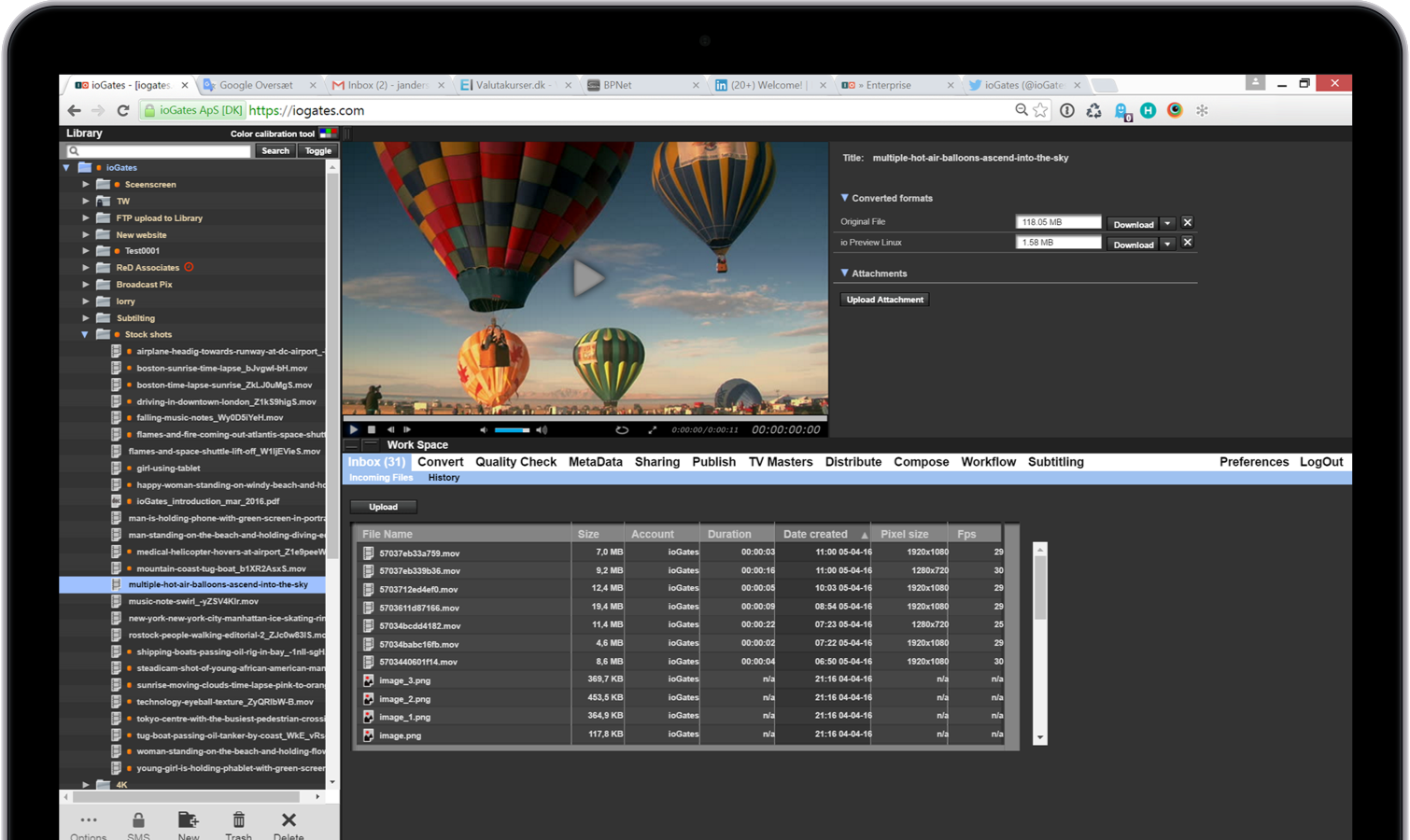
- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 18 September 2020 12:47

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Thursday, 03 September 2020 14:59

- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Friday, 18 September 2020 12:38
- Written by Augustine
- Category: September 2020 - Cybersecurity & Data Safety: perpetual awareness and innovation presupposed
- Thursday, 03 September 2020 14:20