- Category: August 2013 - Data Protection & Security
 According to Veeam’s ten page whitepaper "Five Fundamentals of Modern Data Protection" the protection of company data has become a “given” for most company executives - including CFOs and many CIOs. Just because backup software has been purchased and IT staff salaries are being paid, companies assume that critical data and the applications that manage it are protected. Sadly, in many cases this is far from the truth.
According to Veeam’s ten page whitepaper "Five Fundamentals of Modern Data Protection" the protection of company data has become a “given” for most company executives - including CFOs and many CIOs. Just because backup software has been purchased and IT staff salaries are being paid, companies assume that critical data and the applications that manage it are protected. Sadly, in many cases this is far from the truth.
The paper, which was written by David Davis, provides valuable information, so here‘s the summary.
Protecting your company’s applications and data is much more complex than in the past. With the introduction of virtualization, cloud computing, and many more applications, the aging data protection technology in use by most companies simply isn’t adequate. This results in unnecessary risk for the company and unnecessary pain for IT administrators. Thus, don’t take data protection for granted and have a look at the five fundamentals of modern data protection:
1. Use data protection software built for virtualization
There are hundreds of data protection tools out there, but few of them are “virtualization-savvy”. Legacy data protection tools tend to see every “server” the same way – as a physical server. By incorrectly assuming that all servers are the same, tremendous inefficiencies occur when you attempt to backup or recover applications and data. Data protection tools that are built for virtualization can talk directly to the virtual infrastructure. Through this communication, these data protection tools gain:
- Knowledge of virtual machines (VMs) and the hosts they run on;
- Knowledge of virtual storage to know what needs to be backed up;
- Ability to snapshot VMs and back them up with no downtime;
- Ability to backup only those VM disk blocks that have changed to drastically reduce backup times and the amount of backup data (referred to as “changed block tracking”).
This interaction also becomes a gateway to additional features that you might not expect from your virtual environment, much less from your backup software, including creating virtual lab environments where backups can be automatically tested or used to selectively recover application data. Some legacy data protection tools have been adapted to recognize the virtual infrastructure, but none was built specifically with virtualization in mind. With more and more servers being virtualized, the smart play is to select a data protection tool that is built for virtualization and, because of that, can offer you the most flexibility, functionality and efficiency.
2. Select an agentless data protection solution
Legacy data protection tools require you to install one or more agents on every VM that you need to protect. However, there are downsides to agents, including:
- They require a new piece of software installed on every VM. If a VM doesn’t have the agents, it is unprotected and vulnerable to data loss.
- They can create conflicts with other applications.
- They are difficult to manage, and it’s difficult to see which VMs do or do not have agents installed.
- They utilize CPU and memory on every VM.
The bottom line is that agents are inefficient, across the board.
Make sure that your data protection tool is able to address all backup and recovery scenarios without the need for an agent. Data protection tools that are built for virtualization can go directly to the hypervisor host or virtual infrastructure management system (vCenter Server or SCVMM), find out the names and locations of virtual disks, and then backup those VMs – all without agents. That means that you won’t have to install and maintain agents on each VM being protected, your VMs will run more efficiently, and you’ll gain the maximum benefit possible from your virtual infrastructure. There are numerous types of restores available – and none requires an agent.
3. Leverage a layered approach to data protection
Gone are the days of simply backing up your data to tape - and then hopefully storing that tape offsite. Modern data centers use a layered approach to data protection.
This layered approach could include:
- Local backup to disk;
- Storage-based snapshots;
- VM replication – either onsite or offsite;
- Archival to tape or cloud storage.
The goal is to protect your applications and data in as many ways as are available, and to make restores as fast and easy as possible.
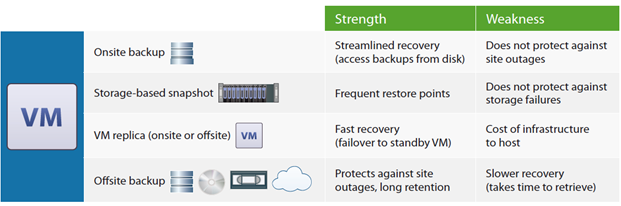
- Immediate access to backups, for instant. = restore of entire VMs, individual files or application data;
- Proven recovery by mounting local backups anytime for automated backup verification and disaster recovery testing;
- Frequent restore points and ability to meet the most aggressive recovery point objectives (RPOs);
- Automated off-site backup and VM replication for disaster recovery (DR);
- Long-term archival to tape or the cloud for a final layer of data protection for peace of mind and audit requirements.
4. Reduce backup data with de-duplication
It’s a fact that the cost of data protection will vary greatly depending on the number and size of VMs you have to protect. Modern data protection tools automatically perform de-duplication as well as compression. De-duplication identifies identical data blocks in source VMs and stores each unique block only once. Since image-based backups used in virtualization capture the entire VM, including the guest operating system (OS), and since the OS is often the same between VMs, there tends to be a lot of duplication.
By using de-duplication, you can tremendously reduce the size of the backup repository, the time to backup VMs, the amount of backup data replicated offsite, and the amount of data sent to tape or cloud storage. Other space-saving features to be on the lookout for include:
- Forever incremental backup – performs an initial full backup but then performs incremental backups, forever.
- Support for hypervisor thin-provisioning – your backup tool should support thin-provisioned disks and maintain thin-provisioning throughout backup, restore and replication operations.
- Exclusion of unneeded data – modern data protection tools should recognize that your VMs are made up of special files such as the configuration file, swap files, snapshot files, and the virtual disk. Not all of those files need to be backed up. You need to be able to specify which of these files you want to exclude from the backup to save time, network bandwidth, and space in the backup repository.
5. Select one solution for multiple hypervisors
The release of Windows Server 2012 Hyper-V has enterprises of all sizes excited about using its advanced features for a very affordable price. However, most enterprises still want to run their tier-1 applications on VMware vSphere. By using both hypervisors in the data center, enterprises can significantly reduce the amount they spend for virtualization software. Whether you are using multiple hypervisors in the data center or not, it’s simply smart to keep your options open. By selecting a data protection tool that can protect both VMware vSphere and Microsoft Hyper-V, you are choosing the tool you need for a multi-hypervisor / tiered-hypervisor infrastructure.
According to David Davis, the job of managing a data center is all about “keeping all the balls in the air”. With a constant flow of new applications, new technologies, and new problems, it’s easy to take core data center responsibilities, such as data protection, for granted. Modern data protection knows virtualization is agentless, uses a layered approach, includes features to reduce the size of the backup repository, and protects VMs on the most popular virtualization platforms. (Source: www.veeam.com)
By MediaBUZZ


